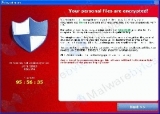
Ransomware attacks – how to protect your business
The number of ransomware attacks is increasing at an alarming rate, making ransomware the biggest cyber threat that businesses are facing today. To see this disturbing trend, you only have to turn back the clock to the beginning of 2016. There was a 30 percent increase in the number of ransomware attacks in the first …
Ransomware attacks – how to protect your business Read More »